About Me
- venux
- im just ordinary people who love IT so much
Followers
page view
hits
venux. Powered by Blogger.
Saturday, 22 January 2011
Conficker
Conficker, also known as Downup, Downadup and Kido, is a computer worm targeting the Microsoft Windows operating system that was first detected in November 2008. It uses flaws in Windows software and Dictionary attacks on administrator passwords to co-opt machines and link them into a virtual computer that can be commanded remotely by its authors. Conficker has since spread rapidly into what is now believed to be the largest computer worm infection since the 2003 SQL Slammer,with more than seven million government, business and home computers in over 200 countries now under its control. The worm has been unusually difficult to counter because of its combined use of many advanced malware techniques.
(source:wp)
Thursday, 20 January 2011
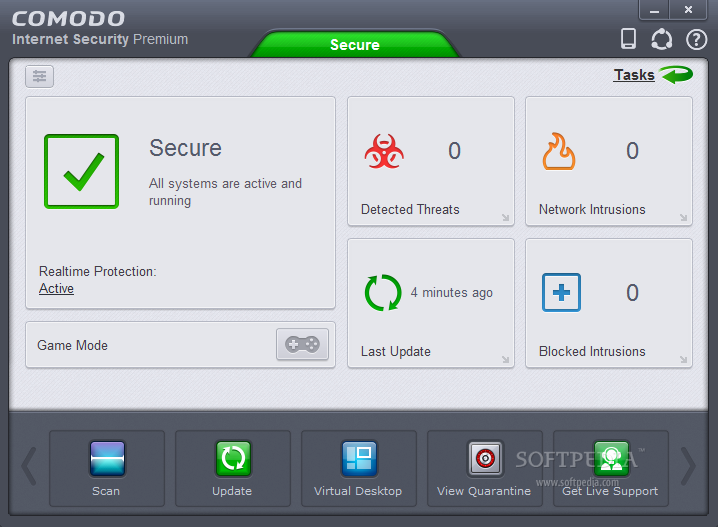
COMODO Internet Security Premium 5.3.45685.1236 (the best antivirus for me)
Comodo Internet Security was developed to be a free, multi-layered security application that keeps hackers out and personal information in.
Built from the ground upwards with your security in mind, Internet Security offers 360° protection by combining powerful Antivirus protection, an enterprise class packet filtering firewall, and an advanced host intrusion prevention system called Defense+.
Unlike the stripped down versions of commercial software that other software vendors offer for free, this is the full, completely functional version of the product.
(source:www.softpedia.com )
Alman virus
Virus Alman approximately 40KB in size, barely visible if it infects executable files. Alman virus is attached to the extension exe files and programs can continue to operate without you knowing the program has been infected.
Monday, 17 January 2011
coolface
An Indonesian-made virus capable of spreading the virus to your e-mail address in the computer, the victim was at risk of libel as a disseminator virus.Virus taxable is known by the nickname 'the face of cool' aka 'Mr Coolface'. The nickname arose because the computer is infected with this virus always led to the writing MR_COOLFACE! when the user opens the Run menu in the Start Menu view.
virus called Worm: w32/Ridnu.B will increasingly dangerous when he finds the address book in your e-mail the victim. Mr. Coolface will automatically send itself to e-mail addresses listed, the risk of victims could be considered as a virus spreader.
Additionally, when the active virus is also able to use all the resources the victim's computer by opening many windows on the task bar of Windows Explorer, so the victim can not prevent this virus when writing messages.
So how do we know that the folder extension. scr? The trick is to display the 'Hidden files and folders' on the Options menu in Windows Explorer, and remove check mark from 'Hide files extensions for known file types'.
When you are exposed to this virus, you should immediately isolate the computer from the network. If your computer is connected to the Internet network, the virus will immediately send copies of itself to all e-mail addresses in your address book. Defamation can be inevitable.
Worm
Computer worms (worm) in computer security, is a computer program that can reproduce itself by itself within a computer system. A worm can reproduce itself by utilizing a network (LAN / WAN / Internet) without interference from the users themselves. Worms do not like a regular computer virus, which multiplies by inserting the program itself to existing programs in the computer, but the worms exploit a security hole that is open, or better known as vulnerability. Some worms also consume the available bandwidth. Worm is an evolution of computer viruses. Only one way to overcome the worm is to close the security hole open, with how to update a patch or service pack of the operating system used with the patch or the most recent Service Pack.
A computer virus can indeed infect files in a computer system, but the worm can do it better. In addition to spread within a system, the worm also can spread to many systems through networks connected to the infected system. Some worms, also can include a virus code that can destroy files, steal documents, e-mail, or do other destructive things, or just make the infected system is useless.
Some examples of the worm are as follows:
* ADMw0rm: The worm that can do the exploitation of network services the Berkeley Internet Name Domain (BIND), by doing a buffer-overflow.
* Code Red: Worm that can make the exploitation of the service Internet Information Services (IIS) version 4 and version 5, with a buffer-overflow attacks.
* Loveletter: worm that spreads by sending itself via e-mail to all accounts listed in the Address Book or Microsoft Outlook Express / Microsoft Outlook contacts list in the code by using Visual Basic Script (VBScript).
* Nimda
* SQL-Slammer
A computer virus can indeed infect files in a computer system, but the worm can do it better. In addition to spread within a system, the worm also can spread to many systems through networks connected to the infected system. Some worms, also can include a virus code that can destroy files, steal documents, e-mail, or do other destructive things, or just make the infected system is useless.
Some examples of the worm are as follows:
* ADMw0rm: The worm that can do the exploitation of network services the Berkeley Internet Name Domain (BIND), by doing a buffer-overflow.
* Code Red: Worm that can make the exploitation of the service Internet Information Services (IIS) version 4 and version 5, with a buffer-overflow attacks.
* Loveletter: worm that spreads by sending itself via e-mail to all accounts listed in the Address Book or Microsoft Outlook Express / Microsoft Outlook contacts list in the code by using Visual Basic Script (VBScript).
* Nimda
* SQL-Slammer
Sunday, 16 January 2011
SPYWARE
Spyware is the term information technology in the English language that refers to one form of suspicious software (malicious software / malware) that install themselves into a system to steal user's data.
Definition
Spyware is a derivative of adware, which monitors the browsing habits of users in the Internet to bring in "a myriad of advertising" to the user. However, because the adware is less dangerous (not to theft of data), spyware do it and send the results of which he collected to the author (adware usually only send data to marketing companies).
Spyware is a derivative of adware, which monitors the browsing habits of users in the Internet to bring in "a myriad of advertising" to the user. However, because the adware is less dangerous (not to theft of data), spyware do it and send the results of which he collected to the author (adware usually only send data to marketing companies).
Loss
Data Theft
Most information is taken without permission is habitual users in navigating the Internet, but many also steal personal data, like e-mail address (to send more junk e mail or can be known by the (spam). Additional Cost Internet Usage
The disadvantage of the presence of spyware, in addition to the many annoying ads are a waste of bandwidth and privacy that have been taken away.
Websites with Spyware
In general, websites that provide free services or websites that sell products. Examples are AOL Mail, Grisoft, Ziddu, personal blogs that want to earn more than advertising, like Google Adsense, business formulas, Gather Bloggers, kliksaya, etc
Basically, Spyware is accompanied with PopUp Windows, which of course in addition to consuming more bandwidth, also makes loading your Internet increasingly slow.
Source [www.vip-maskumis.co.cc]
In general, websites that provide free services or websites that sell products. Examples are AOL Mail, Grisoft, Ziddu, personal blogs that want to earn more than advertising, like Google Adsense, business formulas, Gather Bloggers, kliksaya, etc
Basically, Spyware is accompanied with PopUp Windows, which of course in addition to consuming more bandwidth, also makes loading your Internet increasingly slow.
Source [www.vip-maskumis.co.cc]
How to Prevent entry of Adware and Spyware
Some utilities that can be used to hunt down adware, like Ad-Aware from Lavasoft also be chasing spyware, because it is derived from adware spyware. To hunt for spyware, you can use Trend Micro Internet Security, AVG Anti-Spyware, or other anti-spyware program. Just info, AVG Anti-Spyware does not have the Free Version..
Some utilities that can be used to hunt down adware, like Ad-Aware from Lavasoft also be chasing spyware, because it is derived from adware spyware. To hunt for spyware, you can use Trend Micro Internet Security, AVG Anti-Spyware, or other anti-spyware program. Just info, AVG Anti-Spyware does not have the Free Version..
BRONTOK
Brontok or W32/Brontok (better known as Rontokbro) is a computer virus that began spreading in late 2005. The name is taken from the Eagle brontok (Spizaetus cirrhatus) which is widespread in Asia..
Behavior
This virus presents itself with striking. Characteristic of this virus can be seen from the complexity of how it works. He locked the registry editor Microsoft Registry Editor (regedit.exe or Regedt32.exe) and msconfig.exe utility infected computer. Furthermore, he manipulated the antivirus in his time with Cyclic Redundancy Check 32-bit (CRC32), fingerprints or signatures of more than one. The virus is disguised behind the Windows Explorer folder-shaped icon that she made, although actually still in the form of application.
The uniqueness of this virus is out messages to the infected computer. In some variants, the message coming out is 'five moral message', addressed to a dilapidated Indonesian society. Since variants Brontok.Mybro, message out through the DOS or Command Prompt containing insults to the virus and Nobron RomanticDevil.
This virus presents itself with striking. Characteristic of this virus can be seen from the complexity of how it works. He locked the registry editor Microsoft Registry Editor (regedit.exe or Regedt32.exe) and msconfig.exe utility infected computer. Furthermore, he manipulated the antivirus in his time with Cyclic Redundancy Check 32-bit (CRC32), fingerprints or signatures of more than one. The virus is disguised behind the Windows Explorer folder-shaped icon that she made, although actually still in the form of application.
The uniqueness of this virus is out messages to the infected computer. In some variants, the message coming out is 'five moral message', addressed to a dilapidated Indonesian society. Since variants Brontok.Mybro, message out through the DOS or Command Prompt containing insults to the virus and Nobron RomanticDevil.
Variants
Brontok is known to have several variants, among others W32/Brontok-AJ, W32/Brontok-L, W32/Brontok-W, W32/Brontok-D, W32/Brontok-S, and W32/Brontok.Mybro. The virus is created with Visual Basic 6.0 and some variants are also made with Microsoft Visual C + +.
As of October 2006 noted Brontok variants have 60 more.
Brontok is known to have several variants, among others W32/Brontok-AJ, W32/Brontok-L, W32/Brontok-W, W32/Brontok-D, W32/Brontok-S, and W32/Brontok.Mybro. The virus is created with Visual Basic 6.0 and some variants are also made with Microsoft Visual C + +.
As of October 2006 noted Brontok variants have 60 more.
Subscribe to:
Comments (Atom)