About Me
- venux
- im just ordinary people who love IT so much
Followers
page view
hits
venux. Powered by Blogger.
Saturday, 22 January 2011
Conficker
Conficker, also known as Downup, Downadup and Kido, is a computer worm targeting the Microsoft Windows operating system that was first detected in November 2008. It uses flaws in Windows software and Dictionary attacks on administrator passwords to co-opt machines and link them into a virtual computer that can be commanded remotely by its authors. Conficker has since spread rapidly into what is now believed to be the largest computer worm infection since the 2003 SQL Slammer,with more than seven million government, business and home computers in over 200 countries now under its control. The worm has been unusually difficult to counter because of its combined use of many advanced malware techniques.
(source:wp)
Thursday, 20 January 2011
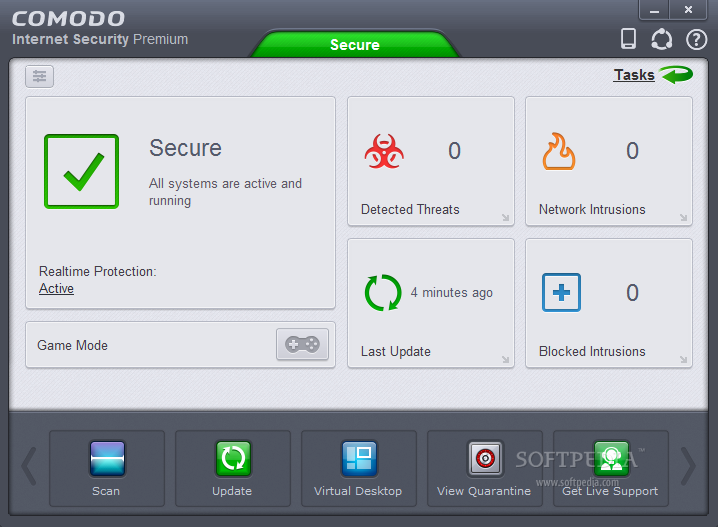
COMODO Internet Security Premium 5.3.45685.1236 (the best antivirus for me)
Comodo Internet Security was developed to be a free, multi-layered security application that keeps hackers out and personal information in.
Built from the ground upwards with your security in mind, Internet Security offers 360° protection by combining powerful Antivirus protection, an enterprise class packet filtering firewall, and an advanced host intrusion prevention system called Defense+.
Unlike the stripped down versions of commercial software that other software vendors offer for free, this is the full, completely functional version of the product.
(source:www.softpedia.com )
Alman virus
Virus Alman approximately 40KB in size, barely visible if it infects executable files. Alman virus is attached to the extension exe files and programs can continue to operate without you knowing the program has been infected.
Monday, 17 January 2011
coolface
An Indonesian-made virus capable of spreading the virus to your e-mail address in the computer, the victim was at risk of libel as a disseminator virus.Virus taxable is known by the nickname 'the face of cool' aka 'Mr Coolface'. The nickname arose because the computer is infected with this virus always led to the writing MR_COOLFACE! when the user opens the Run menu in the Start Menu view.
virus called Worm: w32/Ridnu.B will increasingly dangerous when he finds the address book in your e-mail the victim. Mr. Coolface will automatically send itself to e-mail addresses listed, the risk of victims could be considered as a virus spreader.
Additionally, when the active virus is also able to use all the resources the victim's computer by opening many windows on the task bar of Windows Explorer, so the victim can not prevent this virus when writing messages.
So how do we know that the folder extension. scr? The trick is to display the 'Hidden files and folders' on the Options menu in Windows Explorer, and remove check mark from 'Hide files extensions for known file types'.
When you are exposed to this virus, you should immediately isolate the computer from the network. If your computer is connected to the Internet network, the virus will immediately send copies of itself to all e-mail addresses in your address book. Defamation can be inevitable.
Worm
Computer worms (worm) in computer security, is a computer program that can reproduce itself by itself within a computer system. A worm can reproduce itself by utilizing a network (LAN / WAN / Internet) without interference from the users themselves. Worms do not like a regular computer virus, which multiplies by inserting the program itself to existing programs in the computer, but the worms exploit a security hole that is open, or better known as vulnerability. Some worms also consume the available bandwidth. Worm is an evolution of computer viruses. Only one way to overcome the worm is to close the security hole open, with how to update a patch or service pack of the operating system used with the patch or the most recent Service Pack.
A computer virus can indeed infect files in a computer system, but the worm can do it better. In addition to spread within a system, the worm also can spread to many systems through networks connected to the infected system. Some worms, also can include a virus code that can destroy files, steal documents, e-mail, or do other destructive things, or just make the infected system is useless.
Some examples of the worm are as follows:
* ADMw0rm: The worm that can do the exploitation of network services the Berkeley Internet Name Domain (BIND), by doing a buffer-overflow.
* Code Red: Worm that can make the exploitation of the service Internet Information Services (IIS) version 4 and version 5, with a buffer-overflow attacks.
* Loveletter: worm that spreads by sending itself via e-mail to all accounts listed in the Address Book or Microsoft Outlook Express / Microsoft Outlook contacts list in the code by using Visual Basic Script (VBScript).
* Nimda
* SQL-Slammer
A computer virus can indeed infect files in a computer system, but the worm can do it better. In addition to spread within a system, the worm also can spread to many systems through networks connected to the infected system. Some worms, also can include a virus code that can destroy files, steal documents, e-mail, or do other destructive things, or just make the infected system is useless.
Some examples of the worm are as follows:
* ADMw0rm: The worm that can do the exploitation of network services the Berkeley Internet Name Domain (BIND), by doing a buffer-overflow.
* Code Red: Worm that can make the exploitation of the service Internet Information Services (IIS) version 4 and version 5, with a buffer-overflow attacks.
* Loveletter: worm that spreads by sending itself via e-mail to all accounts listed in the Address Book or Microsoft Outlook Express / Microsoft Outlook contacts list in the code by using Visual Basic Script (VBScript).
* Nimda
* SQL-Slammer
Sunday, 16 January 2011
SPYWARE
Spyware is the term information technology in the English language that refers to one form of suspicious software (malicious software / malware) that install themselves into a system to steal user's data.
Definition
Spyware is a derivative of adware, which monitors the browsing habits of users in the Internet to bring in "a myriad of advertising" to the user. However, because the adware is less dangerous (not to theft of data), spyware do it and send the results of which he collected to the author (adware usually only send data to marketing companies).
Spyware is a derivative of adware, which monitors the browsing habits of users in the Internet to bring in "a myriad of advertising" to the user. However, because the adware is less dangerous (not to theft of data), spyware do it and send the results of which he collected to the author (adware usually only send data to marketing companies).
Loss
Data Theft
Most information is taken without permission is habitual users in navigating the Internet, but many also steal personal data, like e-mail address (to send more junk e mail or can be known by the (spam). Additional Cost Internet Usage
The disadvantage of the presence of spyware, in addition to the many annoying ads are a waste of bandwidth and privacy that have been taken away.
Websites with Spyware
In general, websites that provide free services or websites that sell products. Examples are AOL Mail, Grisoft, Ziddu, personal blogs that want to earn more than advertising, like Google Adsense, business formulas, Gather Bloggers, kliksaya, etc
Basically, Spyware is accompanied with PopUp Windows, which of course in addition to consuming more bandwidth, also makes loading your Internet increasingly slow.
Source [www.vip-maskumis.co.cc]
In general, websites that provide free services or websites that sell products. Examples are AOL Mail, Grisoft, Ziddu, personal blogs that want to earn more than advertising, like Google Adsense, business formulas, Gather Bloggers, kliksaya, etc
Basically, Spyware is accompanied with PopUp Windows, which of course in addition to consuming more bandwidth, also makes loading your Internet increasingly slow.
Source [www.vip-maskumis.co.cc]
How to Prevent entry of Adware and Spyware
Some utilities that can be used to hunt down adware, like Ad-Aware from Lavasoft also be chasing spyware, because it is derived from adware spyware. To hunt for spyware, you can use Trend Micro Internet Security, AVG Anti-Spyware, or other anti-spyware program. Just info, AVG Anti-Spyware does not have the Free Version..
Some utilities that can be used to hunt down adware, like Ad-Aware from Lavasoft also be chasing spyware, because it is derived from adware spyware. To hunt for spyware, you can use Trend Micro Internet Security, AVG Anti-Spyware, or other anti-spyware program. Just info, AVG Anti-Spyware does not have the Free Version..
BRONTOK
Brontok or W32/Brontok (better known as Rontokbro) is a computer virus that began spreading in late 2005. The name is taken from the Eagle brontok (Spizaetus cirrhatus) which is widespread in Asia..
Behavior
This virus presents itself with striking. Characteristic of this virus can be seen from the complexity of how it works. He locked the registry editor Microsoft Registry Editor (regedit.exe or Regedt32.exe) and msconfig.exe utility infected computer. Furthermore, he manipulated the antivirus in his time with Cyclic Redundancy Check 32-bit (CRC32), fingerprints or signatures of more than one. The virus is disguised behind the Windows Explorer folder-shaped icon that she made, although actually still in the form of application.
The uniqueness of this virus is out messages to the infected computer. In some variants, the message coming out is 'five moral message', addressed to a dilapidated Indonesian society. Since variants Brontok.Mybro, message out through the DOS or Command Prompt containing insults to the virus and Nobron RomanticDevil.
This virus presents itself with striking. Characteristic of this virus can be seen from the complexity of how it works. He locked the registry editor Microsoft Registry Editor (regedit.exe or Regedt32.exe) and msconfig.exe utility infected computer. Furthermore, he manipulated the antivirus in his time with Cyclic Redundancy Check 32-bit (CRC32), fingerprints or signatures of more than one. The virus is disguised behind the Windows Explorer folder-shaped icon that she made, although actually still in the form of application.
The uniqueness of this virus is out messages to the infected computer. In some variants, the message coming out is 'five moral message', addressed to a dilapidated Indonesian society. Since variants Brontok.Mybro, message out through the DOS or Command Prompt containing insults to the virus and Nobron RomanticDevil.
Variants
Brontok is known to have several variants, among others W32/Brontok-AJ, W32/Brontok-L, W32/Brontok-W, W32/Brontok-D, W32/Brontok-S, and W32/Brontok.Mybro. The virus is created with Visual Basic 6.0 and some variants are also made with Microsoft Visual C + +.
As of October 2006 noted Brontok variants have 60 more.
Brontok is known to have several variants, among others W32/Brontok-AJ, W32/Brontok-L, W32/Brontok-W, W32/Brontok-D, W32/Brontok-S, and W32/Brontok.Mybro. The virus is created with Visual Basic 6.0 and some variants are also made with Microsoft Visual C + +.
As of October 2006 noted Brontok variants have 60 more.
Trojan Horse
trojan horse or horse troya or more knowledgeable as trojan in computer security refer to a software form suspicious looking (malicious software/malware) that can botch a system or network. aim from trojan is to get information from target (password, recorded user habit in system logarithm, data, and others), and restrain target (gets access right in target).
procedure
trojan differs from software kind suspicious looking another likes computer virus or worm because two matters :
1. "stealth" (invisible and is not see)ed in the operation and oftentimes formed impressing program be program well, temporary computer virus or worm act aggresiveer with botch system or make system is crash.
2. trojan controlleds from other computer(computer attacker).
distribution manner
trojan horse meant to insert codes suspicious looking and botch in a program well and useful; just as in war troya, soldiers sparta hid in horses troya that attributed as dedication to poseidon.
majority trojan in this time shaped a bundle that can be executed (. exe or . com in windows operating system and Dos or program by the name of often executed in operating system unix, like ls, cat, and others) that putted into system at penetrated by a cracker to steal important data for user (password, credit card data, and others). also can infected when does user download application (the frequently of shaped game computer).
detection and cleaning
detect trojan existence is an action rather difficult done. line of least resistance with see port which opened and being in conditon" listening" , by using utility certain a kind of netstat. this matter is caused by many trojans walks as a system service, and work at background, so that trojans can get command from assailant from long distance.
last way is by using an antivirus software, equiped ability to detect trojan that merged with firewalls that monitor every transmission in and out. this way is efficienter, but more expensive, because usually antivirus software merged with firewall has price more expensive, for the alternative you can use a free antivirus that designed to remove trojan horse.
Macro virus
Macro Virus
A "macro," in this context, refers to a small program generally used for automating frequent tasks. Many programs provide some form of scripting language, especially office suite software, such as Microsoft Word or StarOffice. Macro viruses are programs (generally actually worms, not viruses, say the security people) contained within a document and run automatically as part of opening this document. When run, the macro embeds itself in other documents, or otherwise infests the new target system. Some earlier viruses did nothing but spread themselves, or perhaps play a prank. One previous virus simply occasionally replaced words with "Wazoo!".
A macro virus is a computer virus that "infects" a Microsoft Word or similar application and causes a sequence of actions to be performed automatically when the application is started or something else triggers it. Macro viruses tend to be surprising but relatively harmless. A typical effect is the undesired insertion of some comic text at certain points when writing a line. A macro virus is often spread as an e-mail virus. A well-known example in March, 199What is a macro virus?
In response to these early macro viruses, virus software companies began introducing simple filters to scan documents and eliminate viruses before they caused considerable damage, which generally had not been necessary before. 9 was the Melissa virus virus.
The key to preventing damages from macro viruses is the tradeoff from usability to security. Empirically, macro viruses have done an amazing amount of damage, both directly and indirectly. The question is, what usability would we lose by closing these holes? The answer to this question is debated back and forth endlessly. After all, can we really expect end users to know what a macro is, or why they should execute it? In fact, this argument can be turned around. If we are concerned that some users may not be able to activate a macro when they should, why would we think they will know when they shouldn't? Given the huge costs inflicted on everyone by macro viruses, perhaps we should opt for the safer default.
It is interesting to observe that comparable attacks are not found for many other software suites. Market share may explain this difference, making Microsoft's products more obvious targets. But it seems as though there ought to be some problems with other products -- unless the other products are, in fact, more secure.
How to remove
1 ) Open your anti-virus program. If you do not have an anti-virus program, consider downloading Windows Defender or Sophos (see links under Resources). Windows Defender and Sophos are free anti-virus programs.
2 ) Update your anti-virus program. Most anti-virus programs include an "Update" or "Check for Updates" option. Updating your anti-virus is critical. New viruses are found everyday. Thus, if you updated your anti-virus program yesterday, and a new virus is found today, you will not be protected against it.
3 ) Run a full scan of your computer using your anti-virus program. Most anti-virus programs give you the option of running a full scan or a quick scan. A full scan will check your entire computer for viruses, whereas a quick scan only searches the areas where viruses are most likely to be found. If your anti-virus program does not detect and delete the Macro virus, continue to the next step.
Manual Removal
1 ) Press "Ctrl," "Alt" and "Delete."
2 ) Click on the "Task Manager," and then click on the "Processes" tab
.
3 ) End all of the processes associated with the Macro virus. To end a process, right-click on it and select "End Process." To determine if a process is associated with the Macro virus, type the name of the process into the Process Library search box (see links under Resources).
4 ) Click on the "Start" menu, and then click on the "Search Programs and Files" box.
5 ) Search for and delete all of the files associated with the Macro virus. To delete a file, right-click on it and select "Delete." For a list of files associated with the Macro virus, type the name of the Macro virus into the 411-Spyware search box (see links under Resources). If you do not know the name of the Macro virus, you can type the name of suspicious files into the Filename search box to determine if they are associated with a known virus (see links under Resources)
story of computer virus
Before network computer expansion, most viruses were spreaded through removable media, such as floppy disks. These viruses infected programs stored in the disks, while others were inputted into the disk boot sectors, and activated when the user booted the computer from the disk. The traditional and typical virus characteristics common to us now emerged in the 1980s, where there was an increase of BBS (Bulletin Board System, where a computer system runs software that allows users to dial into the system over a phone line), modem use, and software sharing. BBS contributed greatly to the rapid spread of Trojan horses, and viruses were orginally written to target popular software traders. Traders who were in a hurry to retrieve the lastest software were usually the easiest prey to infect viruses with.
The first PC virus was a boot sector virus named (c)Brain. Two brothers, Basit and Amjad Farooq Alvi, whose only intentions were to protect their work from piracy and to target copyright infringers, programmed it. However, according to analysts, the Ashar virus, which was a variant of Brain, possibly was created before the (c)Brain.
The first computer virus to openly make it to the public was a program called “Elk Cloner”. It was created by Rich Skrenta, a computer programmer who was in high school when this virs was created in 1982. Elk Cloner attached itself to the Apple DOS 3.3 operating system and was later spreaded by a floppy disk. When the virus was created, it was intentionally made as a joke by the high school student, who inputted the virus into a game in which the virus was set off after the 50th time of using the game. When the virus was set off, a blank screen appeared and displayed a poem about the virus. The computer then became infected.
In the mid 1990s, macro viruses came into the scene and became common quickly. Ironically, some versions of Microsoft Word allowed the macro virus to multiply and gain additional blank lines. This can cause a misleading detection, as others would see the new strands of the macro virus as a new virus.
Viruses then began spreading via instant messaging. Typically, it sends a web address to everybody in the contact list, and anyone who so much as click on the link would be prone of an immediate infection. However, there are thousands and thousands of viruses operating online and new viruses are discovered every single day.
The first PC virus was a boot sector virus named (c)Brain. Two brothers, Basit and Amjad Farooq Alvi, whose only intentions were to protect their work from piracy and to target copyright infringers, programmed it. However, according to analysts, the Ashar virus, which was a variant of Brain, possibly was created before the (c)Brain.
The first computer virus to openly make it to the public was a program called “Elk Cloner”. It was created by Rich Skrenta, a computer programmer who was in high school when this virs was created in 1982. Elk Cloner attached itself to the Apple DOS 3.3 operating system and was later spreaded by a floppy disk. When the virus was created, it was intentionally made as a joke by the high school student, who inputted the virus into a game in which the virus was set off after the 50th time of using the game. When the virus was set off, a blank screen appeared and displayed a poem about the virus. The computer then became infected.
In the mid 1990s, macro viruses came into the scene and became common quickly. Ironically, some versions of Microsoft Word allowed the macro virus to multiply and gain additional blank lines. This can cause a misleading detection, as others would see the new strands of the macro virus as a new virus.
Viruses then began spreading via instant messaging. Typically, it sends a web address to everybody in the contact list, and anyone who so much as click on the link would be prone of an immediate infection. However, there are thousands and thousands of viruses operating online and new viruses are discovered every single day.
Subscribe to:
Comments (Atom)